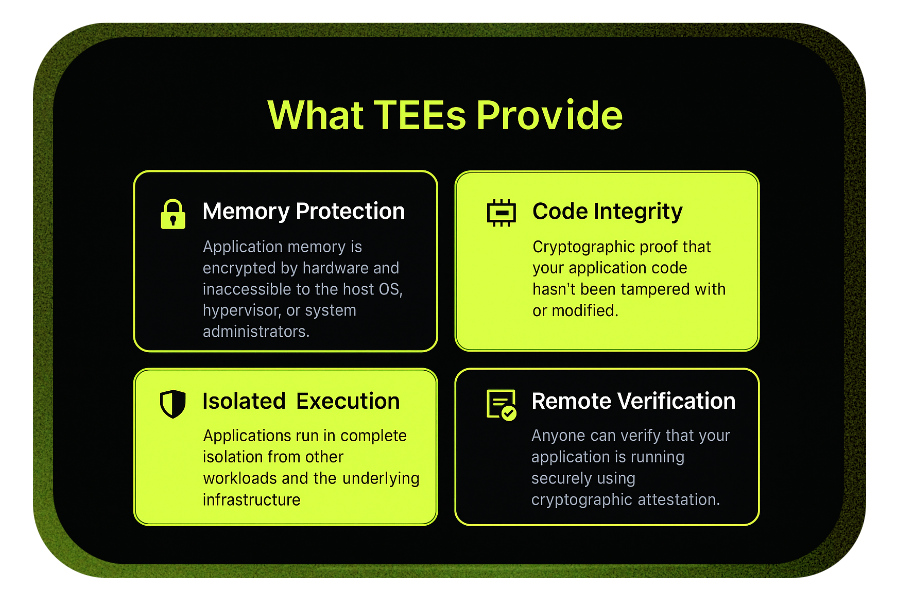
Understanding TEEs and Confidential Computing
At its core, dstack leverages Trusted Execution Environments - hardware-secured computing environments that protect your code and data even from privileged system access. Think of a TEE as a hardware-enforced safe room for your applications. Current TEE Support: dstack currently supports Intel TDX (Trust Domain Extensions) with planned support for AMD SEV-SNP and ARM Confidential Compute Architecture.DStack main components
dstack’s architecture centers around five primary components that work together to provide secure deployment:| Component | Primary Role | When You’ll Use It |
|---|---|---|
| dstack-vmm | Manages TEE virtual machines | Every deployment |
| dstack-gateway | Secure HTTPS gateway | Web-accessible applications |
| dstack-kms | Cryptographic key management | Secure data handling |
| dstack-guest-agent | Container management in TEE | Runtime operations |
| dstack-os | Minimal secure operating system | TEE environment foundation |
The DStack Approach
dstack abstracts the complexity of TEE deployment through a familiar Docker-centric workflow:
- Start with existing containers – Use your current Docker containers and compose files
- Deploy to secure infrastructure – dstack handles TEE provisioning and configuration
- Get automatic security – Memory encryption, attestation, and secure networking included
- Verify independently – Cryptographic proof of security available to anyone
Security Model
dstack implements a zero-trust architecture where security doesn’t depend on trusting infrastructure providers, system administrators, or even the host operating system.✅ what we trust
- TEE hardware (cryptographically verified)
- Open-source code (auditable by anyone)
- Blockchain consensus (decentralized verification)
- Mathematical proofs (attestation signatures)
⚠️ what we don’t trust
- Host operating systems
- Cloud providers
- Network infrastructure
- System administrators
- Other applications on the same hardware
see system architecture for more security details
Key Active Technologies
dstack uses several advanced security mechanisms to guarantee the integrity, confidentiality, and portability of workloads across different environments: Remote Attestationremote attestation is central to dstack’s security model. It provides cryptographic proof that the Trusted Execution Environment (TEE) is genuine and that the application code hasn’t been tampered with. This lets any party verify the integrity and authenticity of the TEE and the running code, ensuring the execution context matches expected measurements. This verifiable evidence is essential for building trust in distributed systems and is a core part of confidential computing. Decentralized Key Management
dstack uses decentralized methods to manage cryptographic keys, reducing reliance on any single provider or authority and improving resilience and security. Immutable Deployments
deployments in dstack are immutable, meaning application images and configurations can’t be changed after deployment. This ensures consistency, prevents drift, and makes it easier to verify the integrity of running workloads. for a comprehensive understanding of dstack’s security framework, see the Security Model page. More technical details are available on the Core Components page.
DStack Network Architecture
dstack secures data in transit through a multi-tiered network stack, integrating four distinct security and isolation domains: Public HTTPSEvery public endpoint is fronted by automatically issued and renewed TLS certificates from Let’s Encrypt, delivering browser-to-edge encryption and hands-free domain routing. WireGuard VPN
A lightweight mesh of WireGuard tunnels secures node-to-node traffic, creating a zero-trust backbone that spans clouds, regions, and on-prem clusters with minimal latency overhead. TDX Isolation
Workloads run inside Intel Trust Domain Extensions (TDX) confidential VMs. Each trust domain is hardware-isolated from the host hypervisor and other tenants; network interfaces are scoped and attested before any packet is accepted, blocking spoofing and side-channel attacks. Application
Inside each TDX enclave, containers use standard Docker/Kubernetes networking—services, virtual IPs, and sidecars—so existing micro-services communicate normally while inheriting all lower-layer protections. understanding dstack’s secure networking architecture and traffic routing—see the networking guide
Documentation Navigation
Core concepts reading path – follow this sequence to build comprehensive understanding:①
🧩
Basic Components
Start here. Learn the role of each component and how they work together.
💡 Focus on relationships, not implementation details
②
⚙️
Core Components
Deep dive into configuration, APIs, and technical implementation patterns.
💡 Reference material for deployment and troubleshooting
③
🌐
Networking
Understand secure traffic routing, VPN tunnels, and network isolation.
💡 Critical for production deployments and security
④
🔒
Security Model
TEE fundamentals, attestation, and the cryptographic foundations of trust.
💡 Essential for understanding “why” behind design choices
⑤
🏗️
System Architecture
Complete picture: how everything connects, scales, and operates together.
💡 Big picture view after understanding individual pieces
What if i read everything and want to go even deeper?
Before you jump into the advanced research and security topics, make sure you’ve gone through the next page on the basics of dstack’s core components. understanding how the/kms, /vmm, and /gateway work together will give you much better intuition for the deeper material.
Once you’re comfortable with those, then we recommend moving on to security and research for a look at the underlying security research and design decisions.
